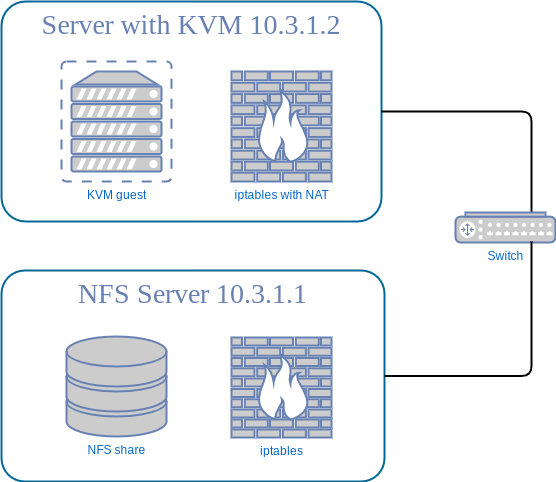
Someday I had to increase storage for an app living inside KVM guest. Considering that this KVM server run almost out of free disk space, probably, the easiest way to achieve the goal was to use NFS to utilize the other server's storage. So, after 'yum install nfs-utils' I tried to mount a share and got the surprise:
# mount.nfs 10.3.1.1:/mnt/nfs-share /mnt/nfs-storage/
Permission denied:/ WTF?
At the same time /var/log/messages on the NFS-server shows:
Feb 5 08:44:07 nfssrv rpc.mountd[47501]: refused mount request from 10.3.1.2 for /mnt/nfs-share (/mnt/nfs-share): illegal port 11447 Feb 5 08:44:09 nfssrv rpc.mountd[47501]: refused mount request from 10.3.1.2 for /mnt/nfs-share (/mnt/nfs-share): illegal port 30047 Feb 5 08:45:22 nfssrv rpc.mountd[47501]: refused mount request from 10.3.1.2 for /mnt/nfs-share (/mnt/nfs-share): illegal port 7666 Feb 5 08:47:00 nfssrv rpc.mountd[47501]: refused mount request from 10.3.1.2 for /mnt/nfs-share (/mnt/nfs-share): illegal port 39260 Feb 5 08:57:21 nfssrv rpc.mountd[47501]: refused mount request from 10.3.1.2 for /mnt/nfs-share (/mnt/nfs-share): illegal port 57330
Fortunately, other people also had this problem and shared their knowledge here: https://serverfault.com/questions/1123448/nfs-mouting-failing-due-to-illegal-port
As far as I understood, some NAT magic (performed by libvirt) leads to source ports for NFS-connections being greater than 1023 (and NFS-daemon doesn't like this). To fix this we need to add 'insecure' option to /etc/exports file on the NFS-server (security implications we will skip for now, we just need things to work :). So it will look like:
$ cat /etc/exports /mnt/iso 10.3.0.0/24(ro,sync,no_root_squash,no_all_squash) /mnt/nfs-share 10.3.1.2(rw,sync,no_root_squash,no_all_squash,insecure)
Then I run 'exportfs -r' to apply the changes and after that the mount command succeeded without issues. Happy end.

0 Responses
Stay in touch with the conversation, subscribe to the RSS feed for comments on this post.
You must be logged in to post a comment.